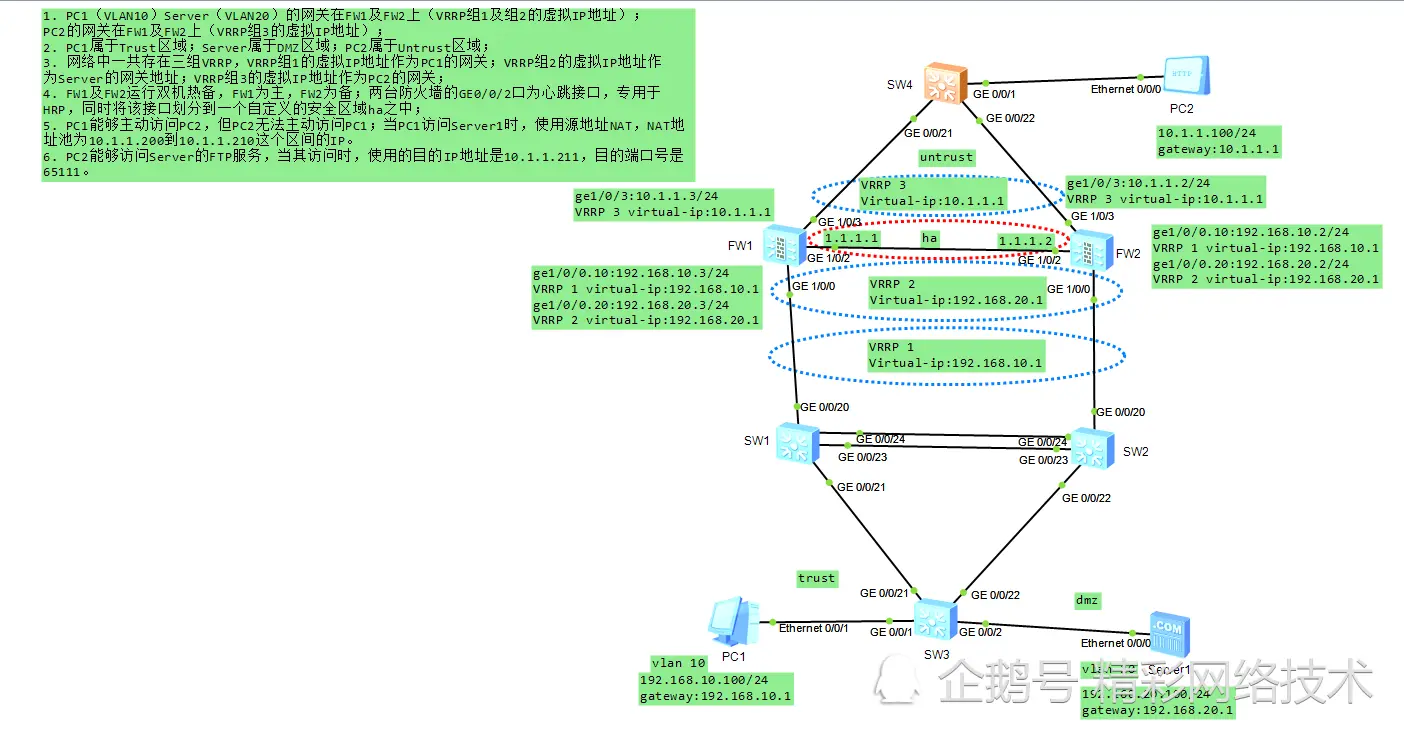
組網要求:
1. PC1(VLAN10)Server(VLAN20)的網關在FW1及FW2上(VRRP組1及組2的虛擬IP地址);PC2的網關在FW1及FW2上(VRRP組3的虛擬IP地址);
2. PC1屬於Trust區域;Server屬於DMZ區域;PC2屬於Untrust區域;
3. 網絡中一共存在三組VRRP,VRRP組1的虛擬IP地址作為PC1的網關;VRRP組2的虛擬IP地址作為Server的網關地址;VRRP組3的虛擬IP地址作為PC2的網關;
4. FW1及FW2運行雙機熱備,FW1為主,FW2為備;兩臺防火牆的GE0/0/2口為心跳接口,專用於HRP,同時將該接口劃分到一個自定義的安全區域ha之中;
5. PC1能夠主動訪問PC2,但PC2無法主動訪問PC1;當PC1訪問Server1時,使用源地址NAT,NAT地址池為10.1.1.200到10.1.1.210這個區間的IP。
6. PC2能夠訪問Server的FTP服務,當其訪問時,使用的目的IP地址是10.1.1.211,目的端口號是65111。
一、eNSP詳解視頻:
二、IP設置:
PC1:192.168.10.100/24,vlan10,網關:192.168.10.1
Server1:192.168.20.100/24,vlan20,網關:192.168.20.1
FW1:ge1/0/0.10:192.168.10.3/24,VRRP 1 virtual-ip:192.168.10.1
ge1/0/0.20:192.168.20.3/24,VRRP 2 virtual-ip:192.168.20.1
ge1/0/3:10.1.1.3/24,VRRP 3 virtual-ip:10.1.1.1
FW2:ge1/0/0.10:192.168.10.2/24,VRRP 1 virtual-ip:192.168.10.1
ge1/0/0.20:192.168.20.2/24,VRRP 2 virtual-ip:192.168.20.1
ge1/0/3:10.1.1.2/24,VRRP 3 virtual-ip:10.1.1.1
三、SW3的主要配置文件:
#
sysname SW3
#
vlan batch 10 20
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/21
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/22
port link-type trunk
port trunk allow-pass vlan 10 20
#
return
四、SW1的主要配置文件:
#
sysname SW1
#
vlan batch 10 20
#
stp instance 0 root primary
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 20
mode lacp-static
#
interface GigabitEthernet0/0/20
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/21
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
eth-trunk 1
#
interface GigabitEthernet0/0/24
eth-trunk 1
#
Return
五、SW2的主要配置文件:
#
sysname SW2
#
vlan batch 10 20
#
stp instance 0 root secondary
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 20
mode lacp-static
#
interface GigabitEthernet0/0/20
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
port link-type trunk
port trunk allow-pass vlan 10 20
#
interface GigabitEthernet0/0/23
eth-trunk 1
#
interface GigabitEthernet0/0/24
eth-trunk 1
#
return
六、FW1的主要配置文件:
#
sysname FW1
#
hrp enable
hrp interface GigabitEthernet1/0/2 remote 1.1.1.2
#
interface GigabitEthernet1/0/0
undo shutdown
undo service-manage enable
#
interface GigabitEthernet1/0/0.10
vlan-type dot1q 10
ip address 192.168.10.3 255.255.255.0
vrrp vrid 1 virtual-ip 192.168.10.1 active
service-manage ping permit
#
interface GigabitEthernet1/0/0.20
vlan-type dot1q 20
ip address 192.168.20.3 255.255.255.0
vrrp vrid 2 virtual-ip 192.168.20.1 active
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.1.1.3 255.255.255.0
vrrp vrid 3 virtual-ip 10.1.1.1 active
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0.10
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/3
detect ftp
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/0.20
#
firewall zone name ha id 4
set priority 90
add interface GigabitEthernet1/0/2
#
firewall detect ftp
#
nat server 0 zone untrust protocol tcp global 10.1.1.211 65111 inside 192.168.2
0.100 ftp
#
nat address-group 1 0
mode pat
section 0 10.1.1.200 10.1.1.210
#
security-policy
rule name TtoU
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name UtoD
source-zone untrust
destination-zone dmz
destination-address 192.168.20.100 mask 255.255.255.255
action permit
rule name TtoD
source-zone trust
destination-zone dmz
destination-address 192.168.20.100 mask 255.255.255.255
action permit
#
nat-policy
rule name TtoD
source-zone trust
destination-zone dmz
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.100 mask 255.255.255.255
action source-nat address-group 1
#
return
七、FW2的主要配置文件:
#
sysname FW2
#
hrp enable
hrp interface GigabitEthernet1/0/2 remote 1.1.1.1
#
interface GigabitEthernet1/0/0.10
vlan-type dot1q 10
ip address 192.168.10.2 255.255.255.0
vrrp vrid 1 virtual-ip 192.168.10.1 standby
#
interface GigabitEthernet1/0/0.20
vlan-type dot1q 20
ip address 192.168.20.2 255.255.255.0
vrrp vrid 2 virtual-ip 192.168.20.1 standby
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.2 255.255.255.0
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.1.1.2 255.255.255.0
vrrp vrid 3 virtual-ip 10.1.1.1 standby
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0.10
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/3
detect ftp
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/0.20
#
firewall zone name ha id 4
set priority 90
add interface GigabitEthernet1/0/2
#
firewall detect ftp
#
nat server 0 zone untrust protocol tcp global 10.1.1.211 65111 inside 192.168.20.100 ftp
#
nat address-group 1 0
mode pat
section 0 10.1.1.200 10.1.1.210
#
security-policy
rule name TtoU
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name UtoD
source-zone untrust
destination-zone dmz
destination-address 192.168.20.100 mask 255.255.255.255
action permit
rule name TtoD
source-zone trust
destination-zone dmz
destination-address 192.168.20.100 mask 255.255.255.255
action permit
#
nat-policy
rule name TtoD
source-zone trust
destination-zone dmz
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.20.100 mask 255.255.255.255
action source-nat address-group 1
#
return
八、驗證結果
1、PC1能正常ping通PC2。
PC>ping 10.1.1.100 -t
Ping 10.1.1.100: 32 data bytes, Press Ctrl_C to break
From 10.1.1.100: bytes=32 seq=1 ttl=126 time=78 ms
From 10.1.1.100: bytes=32 seq=2 ttl=126 time=62 ms
From 10.1.1.100: bytes=32 seq=3 ttl=126 time=78 ms
--- 10.1.1.100 ping statistics ---
3 packet(s) transmitted
3 packet(s) received
0.00% packet loss
round-trip min/avg/max = 62/72/78 ms
2、在SW3——SW1——FW1——FW4的鏈路上斷開,PC1能夠正常Ping通PC2。
3、PC2可以通過ftp 10.1.1.211:65111訪問Server1的ftp服務。
4、PC1訪問Server1時是轉換成10.1.1.200至10.1.1.210的ip地址後訪問server1的
HRP_M[FW2]dis firewall session table
2021-01-22 05:15:08.660
Current Total Sessions : 9
icmp VPN: public --> public 192.168.10.100:24671[10.1.1.208:2056] --> 192.168
.20.100:2048
轉載請超鏈接註明:頭條資訊 » 詳解防火牆VRRP、雙機熱備、NAT、鏈路聚合、MSTP綜合配置
免責聲明
:非本網註明原創的信息,皆為程序自動獲取互聯網,目的在於傳遞更多信息,並不代表本網贊同其觀點和對其真實性負責;如此頁面有侵犯到您的權益,請給站長發送郵件,並提供相關證明(版權證明、身份證正反面、侵權鏈接),站長將在收到郵件24小時內刪除。